Insider trading is a complex form of financial crime. It can be difficult to detect, harder to prove, and highly damaging to market integrity.
For both regulators and firms, each case highlights the same challenge: how to differentiate legitimate trading from activity driven by inside information.
In this article, Per Friberg, Senior Financial Crime Surveillance Officer at Trapets, shares insights from his experience working with over 1,000 insider trading cases, highlighting recurring patterns, real-world examples, and practical detection techniques.
What is insider trading?
Before we get started with real cases and detection techniques, let’s get back to basics to understand what constitutes insider trading under the law.
Insider trading occurs when a person possessing inside information uses it to acquire or dispose of financial instruments to which that information relates. This can involve:
- Trading for one’s own account or on behalf of a third party,
- Cancelling or amending an order, or
- Recommending or inducing another person to trade using inside information.
Insider trading is regulated under the Market Abuse Regulation (MAR) introduced in 2016 in the EU and 2020 in the UK, with only minor differences following Brexit.
To qualify as inside information, all three of the following conditions must be met:
- The information is of a precise nature, relating directly or indirectly to one or more issuers or financial instruments.
- The information has not been made public.
- If made public, the information would likely have a significant effect on the price of the related financial instruments.
Examples of insider trading in practice
Insider trading can take many forms, but most cases follow a recognisable pattern. Information leaks from those with inside information and reaches individuals who act before the information becomes public. The trades are often profitable, well-timed, and difficult to explain through normal market behaviour.
Example case 1: Trading ahead of the ICA Gruppen takeover
In October 2021, a store manager at ICA Maxi sold holdings in fixed-income funds worth approximately SEK 25 million and used the proceeds to purchase ICA Gruppen shares.
Just a few weeks later, in November, a takeover bid for ICA Gruppen was publicly announced.
Subsequent investigation revealed a close connection between the trader and another ICA Maxi store manager, who was classified as an insider within the company.
This case highlights a common pattern: the use of personal or professional relationships to access non-public information.
The red flag in this example represents that the store manager sold off a large holding in zero-risk fixed-income holdings to buy one stock, not even spreading the risk.
For surveillance officers, identifying links between traders and insiders, even those outside the core corporate circle, is necessary in uncovering such activity.
Example case 2: A chain of trades linked to multiple takeover bids
Another notable case involved a trader, referred to as MZ, who executed a series of profitable trades across several companies in quick succession:
- On 5 November 2019, MZ bought shares in Swedol. Six days later, a takeover bid for Swedol was announced.
- On 16-27 October 2021, MZ bought shares in ICA Gruppen. Two weeks later, a takeover bid for ICA Gruppen was announced.
- Between 28 April and 2 May 2022, MZ bought shares in Swedish Match. Only nine days later, a takeover bid for Swedish Match was announced.
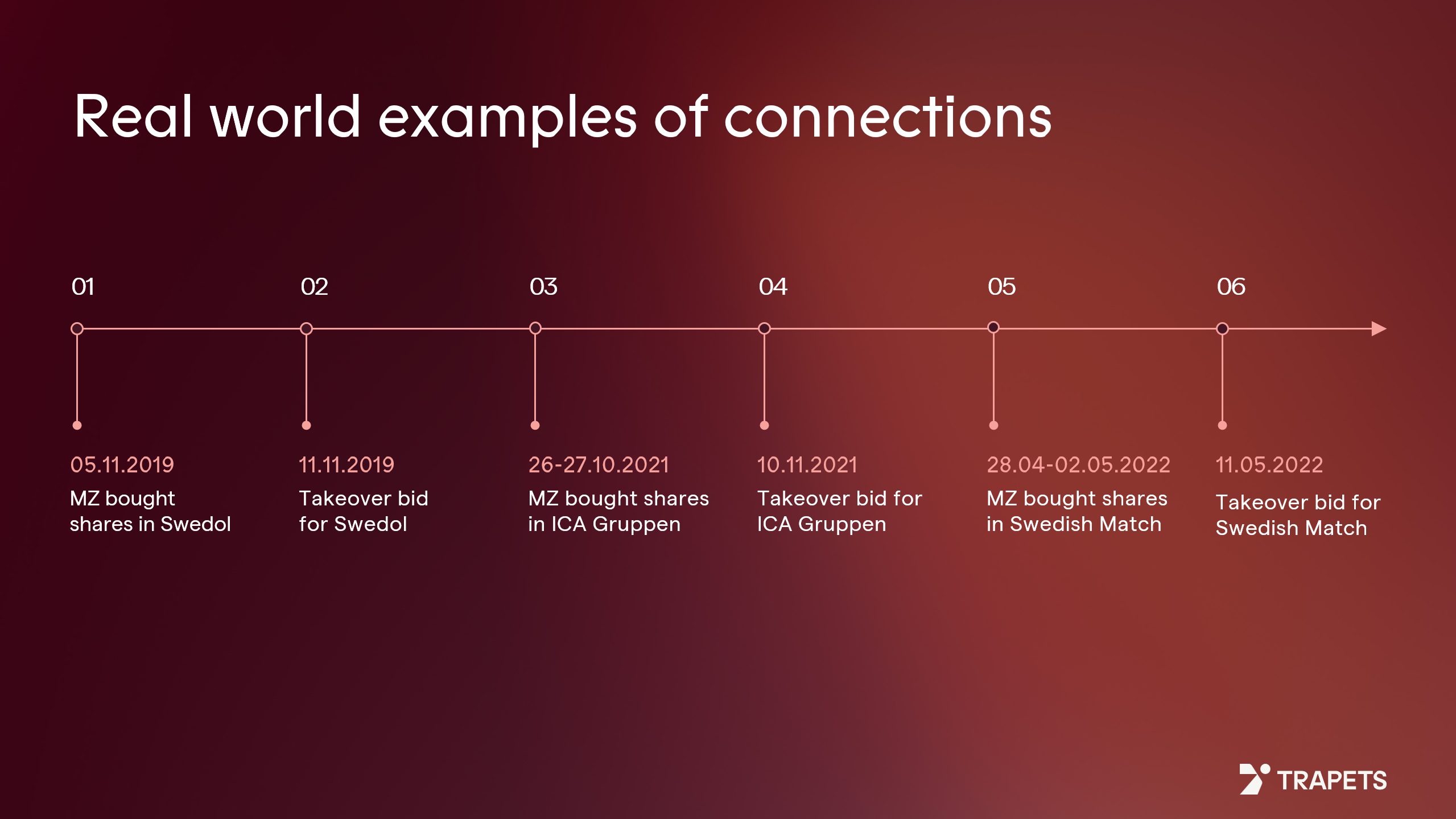
The red flag in this example is that we see too many timely trades ahead of takeover bids, which can’t be simply associated with luck.
Investigators later discovered that MZ was a childhood friend of a surveillance analyst at the marketplace where these shares were trading, someone with access to inside information for all three deals. The consistent pattern and timing made the trades difficult to justify as coincidence.
This case shows the importance of cross-case analysis and relationship mapping, which helps to identify repeated suspicious trading connected to the same social or professional network.
How to identify insider trading using Trapets Market and Trade Surveillance
Insider trading detection often starts with a pattern. Using Trapets Market and Trade Surveillance, compliance teams can visualise and analyse those patterns to uncover potential misuse of inside information.
Insider trading example: Trading ahead of scheduled news
The first example that you see in the graph below is an example of trading ahead of scheduled news. In this case, the system detected aggressive selling activity shortly before a company’s earnings report was published.
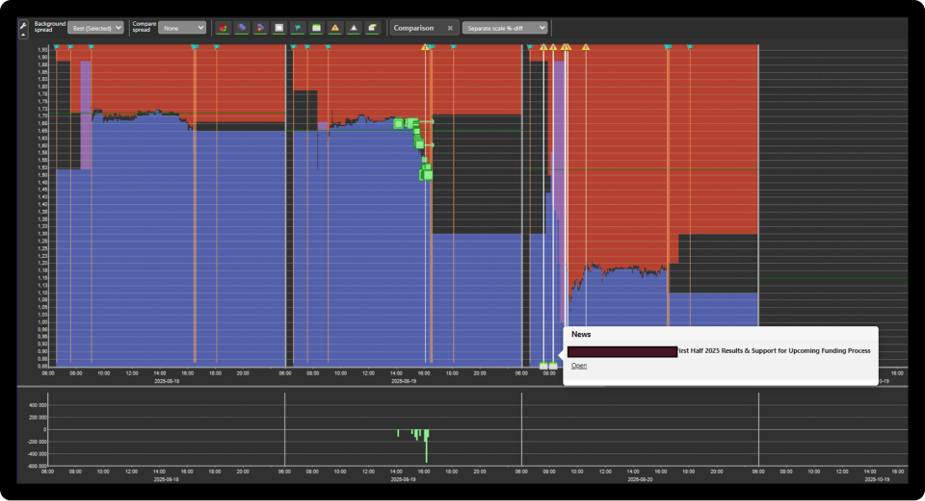
As Per Friberg notes:
“The typical insider is often quite eager to buy or sell ahead of the news. Aggressive trading behaviour is common.”
The trades, visualised as green dots in the surveillance graph, showed a clear sell-off immediately prior to the announcement, a signal that drew attention due to its size and timing. The absence of any public information that could justify the move strengthened the suspicion of insider involvement.
Insider trading example: Trading ahead of unexpected news
The next example is linked to an unexpected takeover announcement.
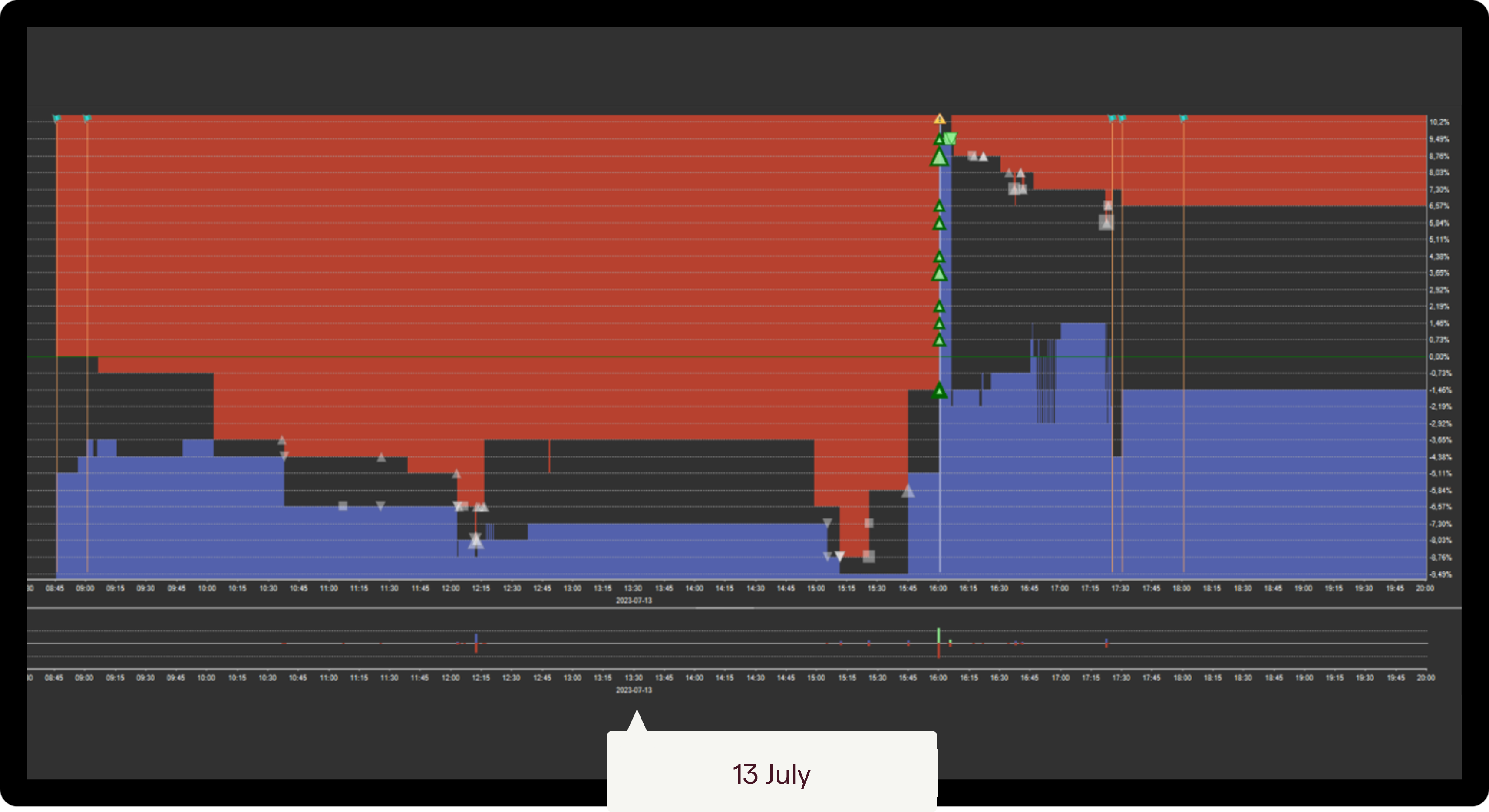
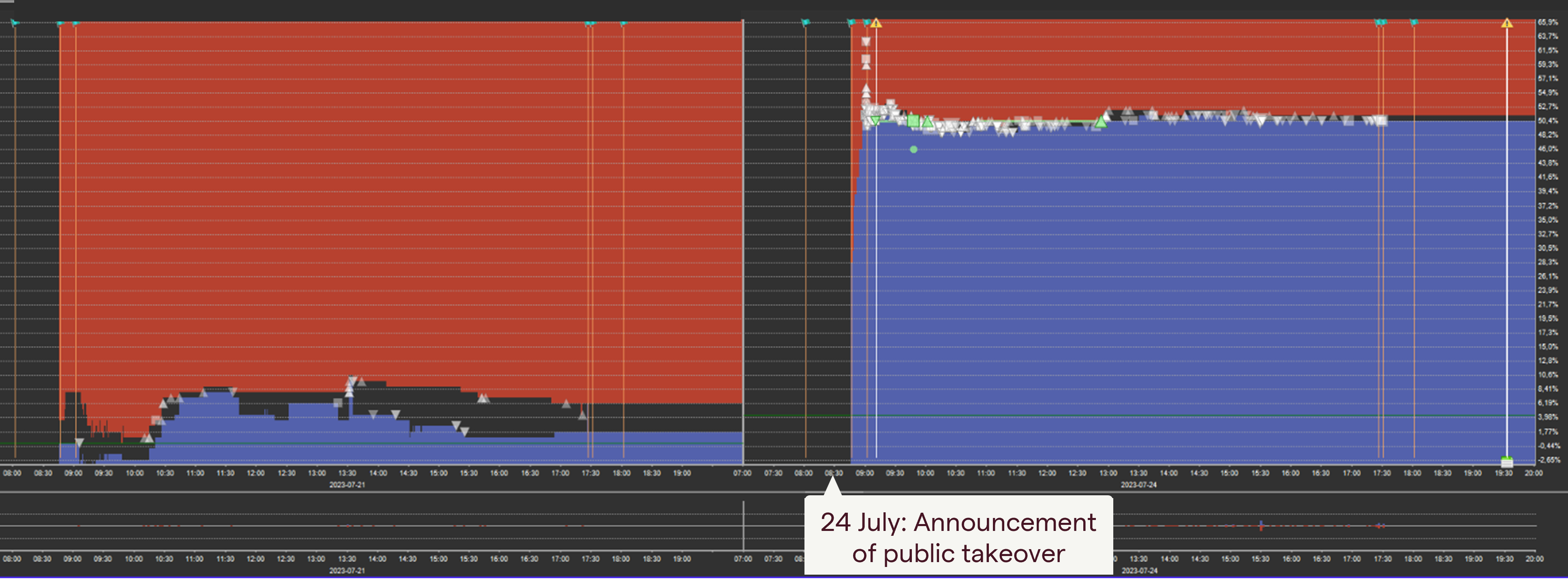
On 13 July, an account began buying aggressively, pushing the price from 2.70 to 3.00. There was no public information or news to explain this sudden price movement.
Eleven days later, on 24 July, a public takeover offer for the same company was announced. The closing price before the news was 2.35, while the offer price stood at 3.53, a premium of nearly 50%.
Immediately after the announcement, the account sold off its holdings at around 3.40, securing a significant profit.
Best practices for compliance teams
Based on experience from over a thousand investigations, Per shared some core practices for detecting insider trading more effectively:
- Always use several different sources of information to find an explanation for a significant price movement. Are there any price-sensitive news?
- Analyse the news to determine if it was inside information before it was made public.
- Try to figure out how long the inside information has existed to determine how far back you should look for suspicious trading.
- For scheduled news, such as earnings reports, look for suspicious trading closely ahead of the publication.
- For unexpected news, such as a public takeover bid, a profit warning or a business breakthrough, look further back depending on the type of news. Suspicious trading ahead of a public takeover bid could have taken place several months before it was made public.
- Remember to analyse trading in underlying instruments, such as options, warrants, mini futures, and so on.
- When something stands out as suspicious, analyse the trading history for that account and look for other red flags, such as taking a greater risk or trading larger than usual, no previous trades in the instrument, quick profit taking, and trading on several accounts.
- Look for aggressive orders and non-price-sensitive trading.
- Look for any obvious connections between the account holder behind the suspicious trading and the issuer of the instrument.
Final thoughts
“Insider trading undermines market integrity and exposes firms to severe legal and reputational consequences. By combining proactive monitoring, strong access controls, and advanced detection technology, you can turn compliance from a defensive function into a strategic safeguard,” summarised Per Friberg in a previous webinar.
For surveillance professionals, each suspicious trade is an opportunity to detect wrongdoing and strengthen trust in the market.
Curious how you can use technology to spot insider trading? Watch the webinar where Per shares methods on how to identify insider trading, or contact us to discover how Trapets Market and Trade Surveillance can help you enhance your market monitoring efforts.


